How To Install OpenVPN in FreeBSD
OpenVPN is a an open source software application that implements virtual private network (VPN) solutions for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. OpenVPN uses SSL/TLS security for encryption and is capable of traversing network address translators and firewalls.
I. OpenVPN Server - Installation and Configuration
1. Installing OpenVPN Server
To install OpenVPN from FreeBSD ports, enter:
cd /usr/ports/security/openvpn make install clean
2. Configuring OpenVPN Server
Create configuration directory and copy all OpenVPN configurations:
mkdir -p /usr/local/etc/openvpn/keys cp -R /usr/local/share/doc/openvpn/ /usr/local/etc/openvpn/ cd /usr/local/etc/openvpn
3. Generating Encryption Certificates
cd /usr/local/etc/openvpn/easy-rsa/2.0 chmod +x * sh . ./vars sh ./clean-all
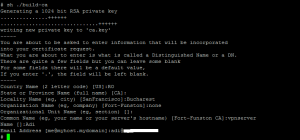
Generate ca.key
sh ./build-ca
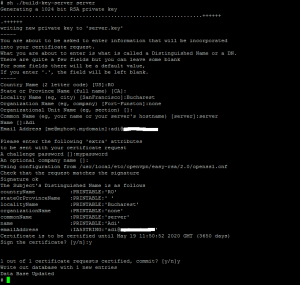
Generate server.key
sh ./build-key-server server
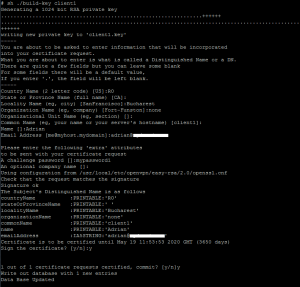
Generate "client1.key" for Client1
sh ./build-key client1
NOTE: If you want to create more clients, just repeat this step and make sure you enter a different "CommonName".
Generate DH parameters 1024 bit
sh ./build-dh
4. Finishing Setup
Copy all files in key directory to /usr/local/etc/openvpn/keys
cp -R keys/* /usr/local/etc/openvpn/keys
List all files in keys directory
ls -al /usr/local/etc/openvpn/keys total 46 drwxr-xr-x 2 root wheel 512 May 22 15:02 . drwxr-xr-x 6 root wheel 512 May 22 14:41 .. -rw-r--r-- 1 root wheel 3883 May 22 15:02 01.pem -rw-r--r-- 1 root wheel 3780 May 22 15:02 02.pem -rw-r--r-- 1 root wheel 1233 May 22 15:02 ca.crt -rw------- 1 root wheel 887 May 22 15:02 ca.key -rw-r--r-- 1 root wheel 3780 May 22 15:02 client1.crt -rw-r--r-- 1 root wheel 725 May 22 15:02 client1.csr -rw------- 1 root wheel 887 May 22 15:02 client1.key -rw-r--r-- 1 root wheel 245 May 22 15:02 dh1024.pem -rw-r--r-- 1 root wheel 219 May 22 15:02 index.txt -rw-r--r-- 1 root wheel 21 May 22 15:02 index.txt.attr -rw-r--r-- 1 root wheel 21 May 22 15:02 index.txt.attr.old -rw-r--r-- 1 root wheel 106 May 22 15:02 index.txt.old -rw-r--r-- 1 root wheel 3 May 22 15:02 serial -rw-r--r-- 1 root wheel 3 May 22 15:02 serial.old -rw-r--r-- 1 root wheel 3883 May 22 15:02 server.crt -rw-r--r-- 1 root wheel 712 May 22 15:02 server.csr -rw------- 1 root wheel 891 May 22 15:02 server.key
Edit server.conf
cp /usr/local/share/doc/openvpn/sample-config-files/server.conf /usr/local/etc/openvpn/ vi /usr/local/etc/openvpn/server.conf
user root port 1194 proto udp mssfix 1400 # This setting fixed problems I was having with apps like Remote Desktop dev tap ca /usr/local/etc/openvpn/keys/ca.crt cert /usr/local/etc/openvpn/keys/server.crt key /usr/local/etc/openvpn/keys/server.key # This file should be kept secret dh /usr/local/etc/openvpn/keys/dh1024.pem server 192.168.254.0 255.255.255.0 #push "route-gateway 192.168.1.1" # push default gateway #push "route 192.168.1.0 255.255.255.0 192.168.254.1" #push "route 192.168.2.0 255.255.255.0 192.168.254.1" ifconfig-pool-persist ipp.txt keepalive 10 120 cipher BF-CBC # Blowfish (default) encryption comp-lzo max-clients 10 # Assign the maximum number of clients here persist-key persist-tun status /var/log/openvpn-status.log log-append /var/log/openvpn.log verb 3 #route 192.168.2.0 255.255.255.0 192.168.254.2
Modify rc.conf
vi /etc/rc.conf
gateway_enable="YES" openvpn_enable="YES" openvpn_configfile="/usr/local/etc/openvpn/server.conf" openvpn_if="tap"
Enable IP Forwarding
sysctl net.inet.ip.forwarding=1
Modify syslog.conf to support OpenVPN log
vi /etc/syslog.conf
### add the lines to the end of the config !openvpn .* /var/log/openvpn.log
Create openvpn.log and reload syslogd
touch /var/log/openvpn.log killall -HUP syslogd
Starting OpenVPN Server
/usr/local/etc/rc.d/openvpn start
II. OpenVPN Client - Installation and Configuration
1. Installing OpenVPN Client
To install OpenVPN from FreeBSD ports, enter:
cd /usr/ports/security/openvpn make install clean
2. Configuring OpenVPN Client and finishing setup
mkdir -p /usr/local/etc/openvpn/keys
You have to transfer ca.crt, client1.crt, client1.key from the OpenVPN server and copy them in the /usr/local/etc/openvpn/keys directory.
vi /usr/local/etc/openvpn/client.conf
client dev tap #tap-mtu 1500 mssfix 1400 proto udp remote 1.2.3.4 1198 # replace 1.2.3.4 with IP Address of the OpenVPN server nobind #user openvpn #group openvpn persist-key persist-tun ca /usr/local/etc/openvpn/keys/ca.crt cert /usr/local/etc/openvpn/keys/client1.crt key /usr/local/etc/openvpn/keys/client1.key #cipher BF-CBC comp-lzo verb 3 mute 20 status /var/log/openvpn-status.log log-append /var/log/openvpn.log #route 192.168.254.3 255.255.255.255 192.168.254.1
Modify rc.conf
vi /etc/rc.conf
openvpn_enable="YES" openvpn_configfile="/usr/local/etc/openvpn/client.conf" openvpn_if="tap"
Modify syslog.conf to support OpenVPN log
vi /etc/syslog.conf
### add the lines to the end of the config !openvpn .* /var/log/openvpn.log
Create openvpn.log and reload syslogd
touch /var/log/openvpn.log killall -HUP syslogd
Starting OpenVPN Client
/usr/local/etc/rc.d/openvpn start
III. Testing the VPN connection
Test connection from the server:
[root@server ~]# ping 192.168.254.2 PING 192.168.254.2 (192.168.254.2) 56(84) bytes of data. 64 bytes from 192.168.254.2: icmp_seq=1 ttl=64 time=85.5 ms 64 bytes from 192.168.254.2: icmp_seq=2 ttl=64 time=83.3 ms 64 bytes from 192.168.254.2: icmp_seq=3 ttl=64 time=93.3 ms --- 192.168.254.2 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 199ms rtt min/avg/max/mdev = 83.363/87.420/93.347/4.298 ms
Test connection from the client:
root@client:~ # ping 192.168.254.1 PING 192.168.254.1 (192.168.254.1): 56 data bytes 64 bytes from 192.168.254.1: icmp_seq=0 ttl=64 time=91.550 ms 64 bytes from 192.168.254.1: icmp_seq=1 ttl=64 time=91.261 ms 64 bytes from 192.168.254.1: icmp_seq=2 ttl=64 time=88.179 ms --- 192.168.254.1 ping statistics --- 3 packets transmitted, 3 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 88.179/90.330/91.550/1.526 ms
 Print This Post
Print This Post